Set up SSO with OneLogin
This section explains how to set up your SSO connection using OneLogin as the identity provider, so that users can sign in to Autodesk with their organization’s email address. This connection uses SAML (Security Assertion Markup Language) to allow Autodesk to communicate with OneLogin to authenticate users. To enable this communication, you will need to add metadata from OneLogin to Autodesk and vice versa.
Page Contents:
Register Autodesk SSO as an app on OneLogin
Add OneLogin metadata to Autodesk
Begin setup in Autodesk
In Autodesk Account, go to User management > By user or By Group.
Select your team from the drop-down list and click the Team Settings ⚙️ icon in the upper right-hand corner.
Go to the section Single sign-on (SSO) and select Manage SSO.
Select Manage SSO tab > Set up connection.
You will be asked to name your connection. Enter a name that will help you easily identify the connection between your identity provider and Autodesk. The name you choose can also help differentiate between connections. The name you choose must be unique and not in use by another team or organization.
Select your identity provider from the drop-down menu.
Register Autodesk SSO as an app on OneLogin
To set up single sign-on you must register Autodesk SSO as a SAML app on OneLogin.
- Sign in to your OneLogin Admin portal using an account that has admin privileges.

The URL for OneLogin differs from company to company. It is of the form https://<your_company_domain_name>.onelogin.com/login
In the navigation pane, click Administration.
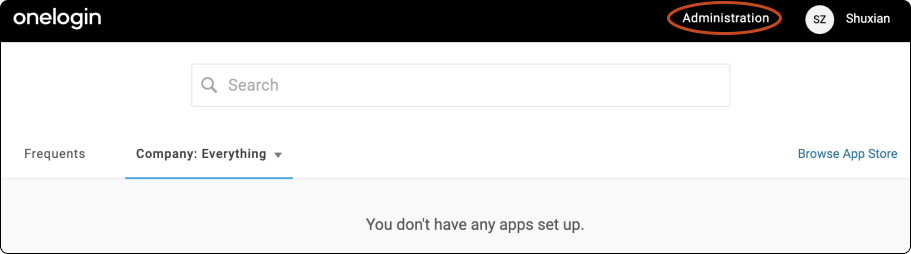
Open Applications from the Applications Menu.
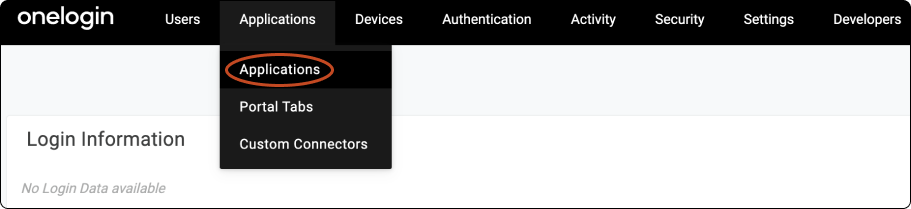
Click Add App.
Note:When you have added an app or two, you can go to Users > Roles to start adding and grouping your users.
Type
Autodesk SSOin the search box, then select the Autodesk SSO application (SP).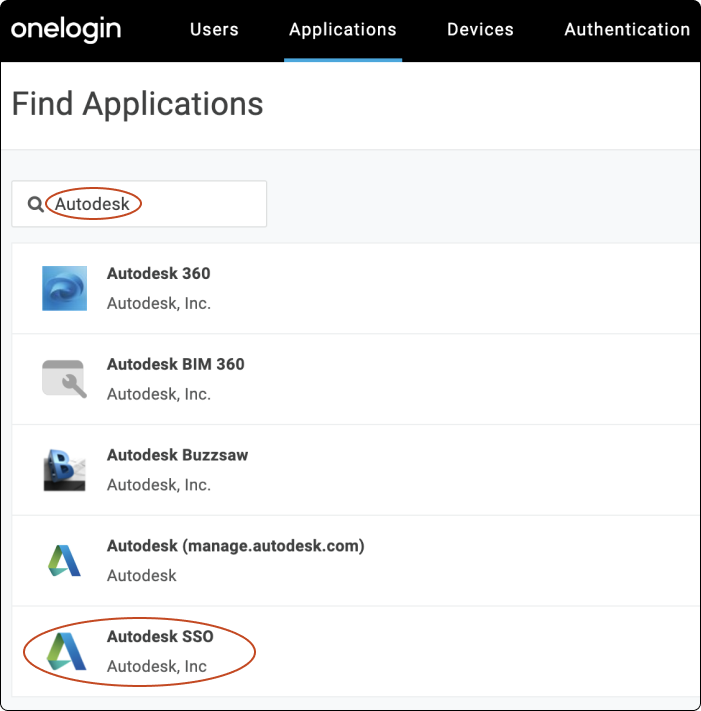 Note:
Note:This application is pre-configured with all the essential settings including the SAML attributes mapping. Refer to the manual configuration procedure in case of any issues with the Autodesk pre-configured template or to view/update the SAML mapping source.
Specify a unique name in the Display Name box and click SAVE.
Note:You can specify any name for establishing the connection. Here we have used
Autodesk SSOfor the Display Name field.
Add OneLogin metadata to Autodesk
This section covers how to get metadata from OneLogin that is needed to set up a SAML connection with Autodesk. You can either choose:
Automatic setup to download the metadata file from OneLogin and upload it to Autodesk (recommended),
Manual setup to copy and paste the information manually.
In the OneLogin portal, go to Applications > Autodesk SSO > SSO.
For automatic setup:
Download the X.509 certificate generated by OneLogin.
Click SSO.
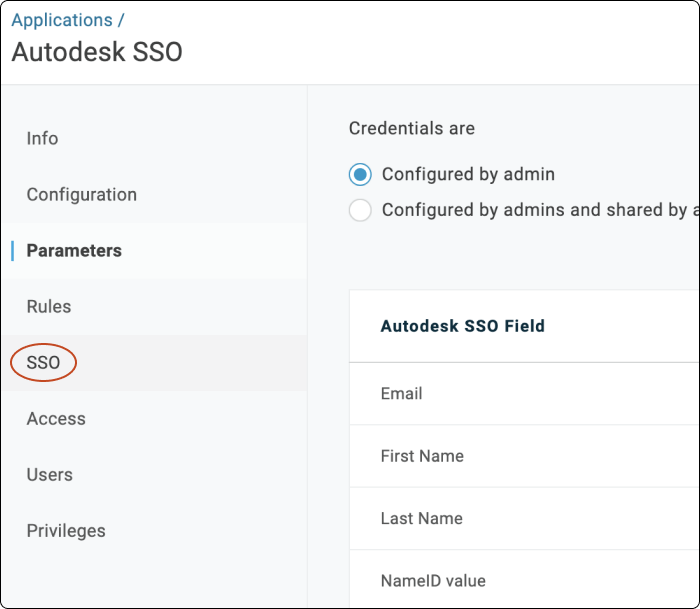
The default sign-on method is SAML 2.0.
On the top-right corner, click More Actions > SAML Metadata to download the XML file.
Switch to Autodesk Account, select Upload to upload the SAML Metadata file which you downloaded from OneLogin.
Confirm that the fields are filled in and click Next.
For manual setup:
Copy Issuer URL and SAML 2.0 Endpoint (HTTP) values.
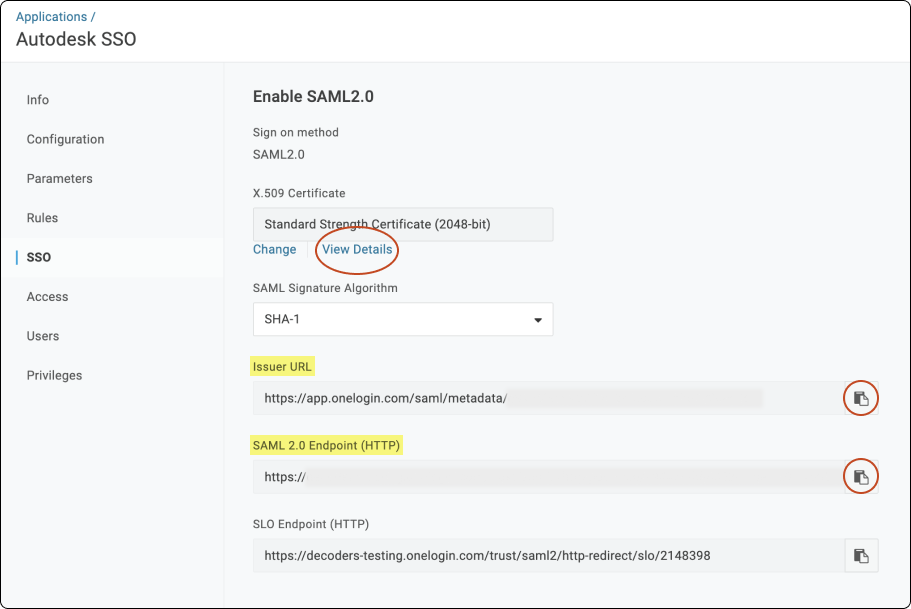
Under SAML Signature algorithm select SHA-512 and click Save > View Details.
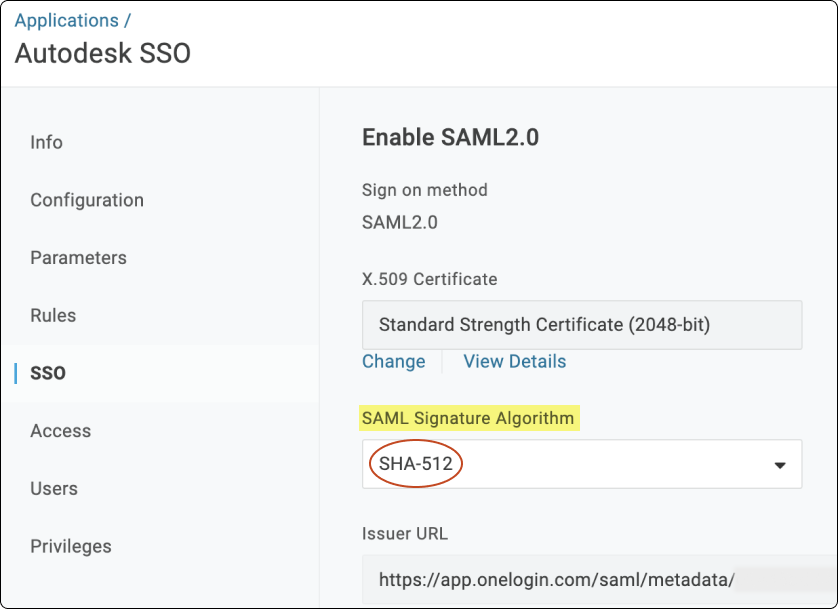
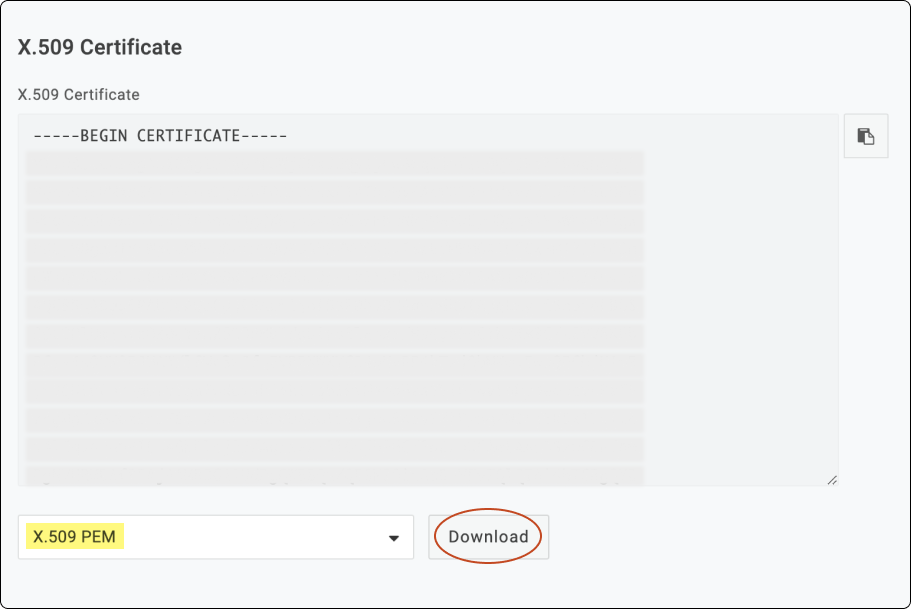
Click Download to save the '.PEM' file.
Enter the information you copied from OneLogin and paste into Autodesk as shown in the table.
OneLogin Autodesk Issuer URL Entity ID SAML 2.0 Endpoint (HTTP) Sign-on URL* X.509 Certificate Verification Certificate Confirm that the fields are filled in and click Next in Autodesk Account.
*Binding refers to the mechanism used to transmit authentication data between the identity provider and service provider (Autodesk). There are two binding methods: Post and Redirect.
The Post method is recommended, and is selected by default. This method transmits SAML messages within an HTML form using base64-encoded content. Because messages are encoded, it is more secure than the Redirect method, and is recommended as a security best practice.
The Redirect method transmits SAML messages encoded as HTTP URL parameters. The response is part of the URL and may be captured and exposed in various logs, making this method less secure than the Post method.
Add Autodesk metadata to OneLogin
This step allows Autodesk to complete the connection with your identity provider for user authentication.
Select Manual setup. Note that you can only select Manual setup here because the OneLogin portal does not have an option to upload metadata file automatically.
In Autodesk, copy the Entity ID and Assertion Customer Service (ACS) URL. OneLogin does not require the verification certificate so you can ignore this field.
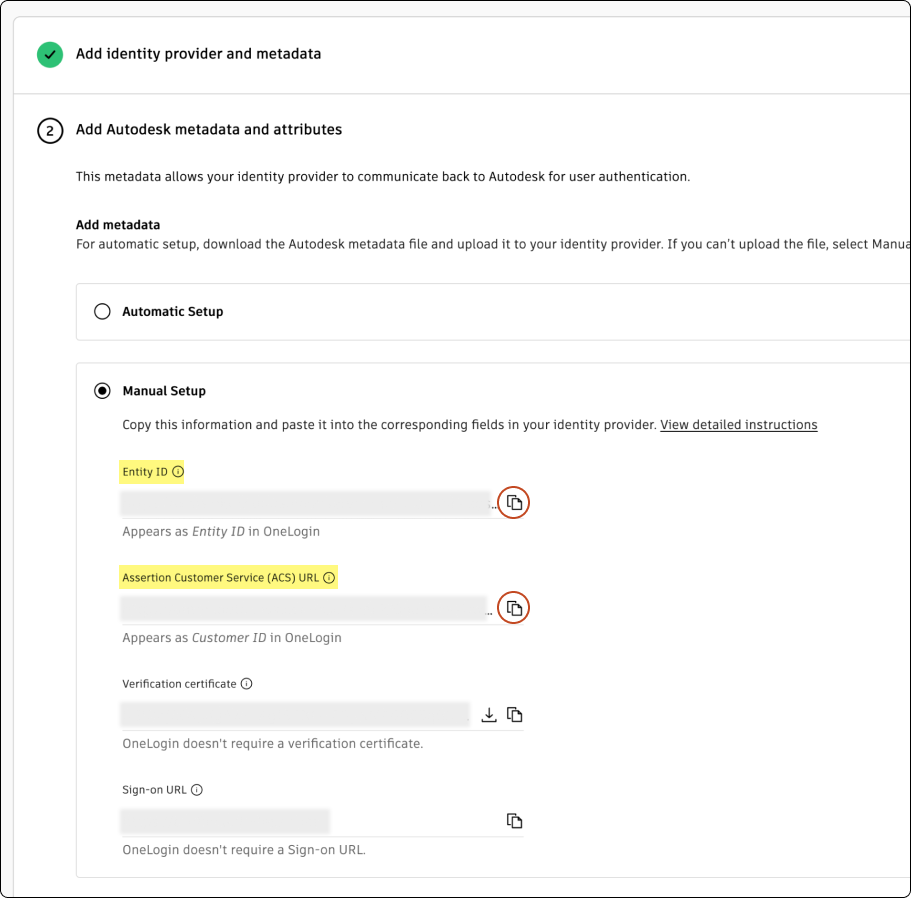
Return to OneLogin.
Enter the information you copied from Autodesk and paste it into OneLogin as shown in the table.
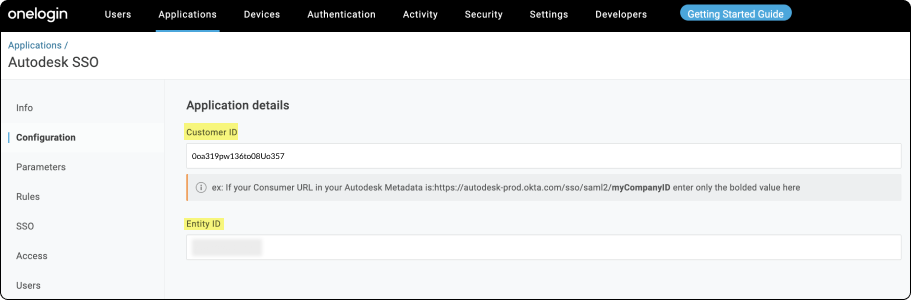
Autodesk OneLogin Entity ID Entity ID Assertion Customer Service (ACS) URL Customer ID In OneLogin Portal > Applications > Autodesk SSO > Configuration
Under Customer ID, enter the company ID, which is usually the last part of the URL from the Location value you noted earlier. In the example https://dev-289038.okta.com/sso/saml2/0oa319pw136to08Uo357, the company ID is 0oa319pw136to08Uo357.
Under Entity ID, enter the entityID value you noted earlier.
Click Save.
Map attributes
Under Parameters > SAML Test Connector, make sure that the user attributes are mapped correctly according to the table.
| OneLogin attributes names | Autodesk attributes |
|---|---|
| First Name | firstName |
| Last Name | lastName |
| OneLogin ID | objectGUID |
The attributes to map are case-sensitive and contain no spaces. Do not map additional attributes. For SSO, the backend does not store any other attributes you may have mapped. However, if you set up directory sync, additional attribute mapping will cause the sync to fail, and you will have to remove the additional attributes.
Test your connection
Before testing the connection, make sure you assign yourself access to the Autodesk SSO application that you created with your identity provider.
Click Test connection to be redirected to your organization’s SSO sign-in page. (If you are not redirected, see Troubleshooting).
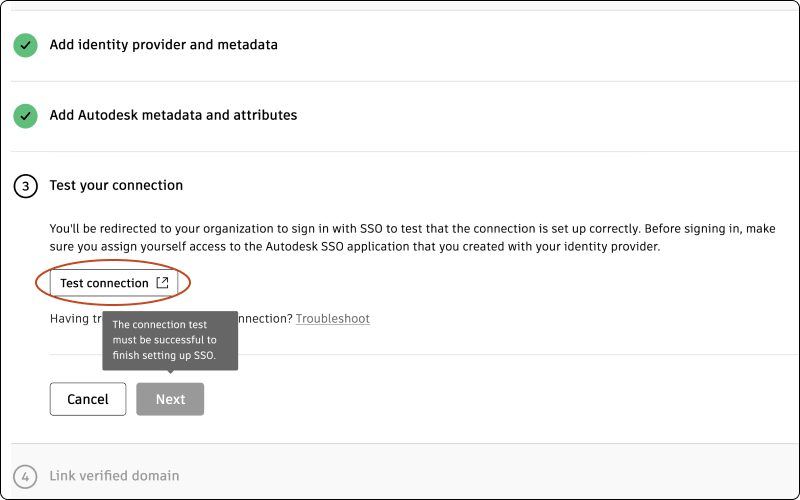
Sign in to make sure that the connection between your identity provider and Autodesk is set up correctly. If the test is successful, you will see the message “Connection Test Result: Success” and a list of properties.
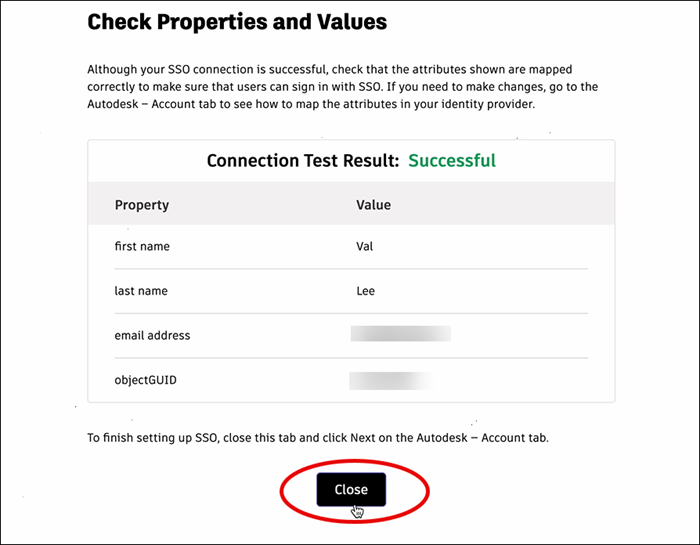
Confirm that the attributes have mapped correctly by comparing the Property and Value columns. The property “first name” should appear next to the user’s first name, “last name” should appear next to the user’s last name, and so on. If you need to make changes, return to the previous step (Mapping attributes) and re-map the attributes.
Once you have confirmed that attributes are mapped correctly, return to the Autodesk Account tab and click Next.
Note:In order to proceed to step 4, which involves linking a verified domain, it is crucial that your connection is tested successfully.
Link verified domains
You will see a list of your verified domains. Select one or more verified domains to link to your connection.
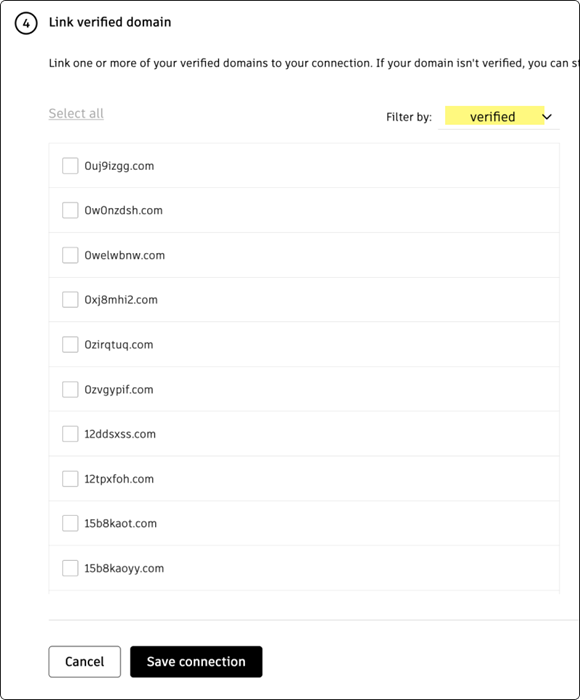
Click Save connection to complete the setup.
If a domain is not verified, you can still save the connection and link it later in Manage SSO.
If you have not finished verifying domains, go to Add and verify domains to complete the process. Once you have finished linking domains, return to Manage SSO to test and turn on SSO.
Previous: Set up your connection
Next: Test and turn on SSO
